SD-WAN with Cyber Security

Small businesses need affordable protection from online attacks, especially those that try to overwhelm their systems.
The Small Business Market
According to a recent Forbes article from Jan 31, 2024 titled “Small Business Statistics Of 2024”, there are over 33 million businesses in the United States, making up 99.9% of all U.S. businesses.
Cost of Business is Rising
- The cost of maintaining a business is increasing due to inflationary pressures.
- Businesses are constantly evaluating their spending and looking to reduce office expenses.
- These businesses are seeking more cost-effective options including leveraging technology to boost productivity and reduce operational downtime.
How Much Business Is Lost When Your Internet Goes Down?
The Cyber Security Problem
Current Cyber Security solutions are designed for big companies and need expensive hardware. These systems use complex techniques that strain the resources of regular office routers. As small businesses shift to using cloud applications, their internet-based services become a target for cyber threats. This is a big worry because attackers can weaken the system with a denial-of-service attack, making them vulnerable.

The Challenges
- Small businesses are more at risk than larger enterprise companies and can be easier targets for cyber attacks.
- Routers and Firewalls with the ability to defend against denial-of-service attacks can be too costly for them.
- These businesses also need SD-WAN (software-defined networking over the internet) for their changing application and always-on Internet demands, which adds to these expenses.
- They simply can’t afford the upfront capital expense for equipment and the high service costs of larger enterprise company solutions.
Small Businesses need SD-WAN & Cyber Security as-a-Service with low monthly licensing fees they can afford.
What is a Denial-of-Service (DOS) Attack?
DOS attacks can slow down a system and prevent new connections. In this situation, the system rejects packets from new legitimate traffic trying to connect.
Main Attack Types & Detections:
Brute Force:
Tries to overwhelm the system by creating lots of network connections with both valid and invalid requests.
Semantic:
Targets specific weaknesses in devices.
Distributed:
Combines brute force and semantic attacks from multiple sources, making it larger and more sophisticated.
Attack Detection:
Detecting DDOS attacks can be complicated and requires more computing power than typical small office or consumer-grade networking devices can handle.
Traditional Detection:
Normally, Network Intrusion Detection Systems (NIDS) work with advanced Firewall devices. These devices use databases and deep packet inspection to identify valid and invalid traffic signatures.
These enterprise type systems are resource-intensive and costly, making them too expensive for small and micro businesses.
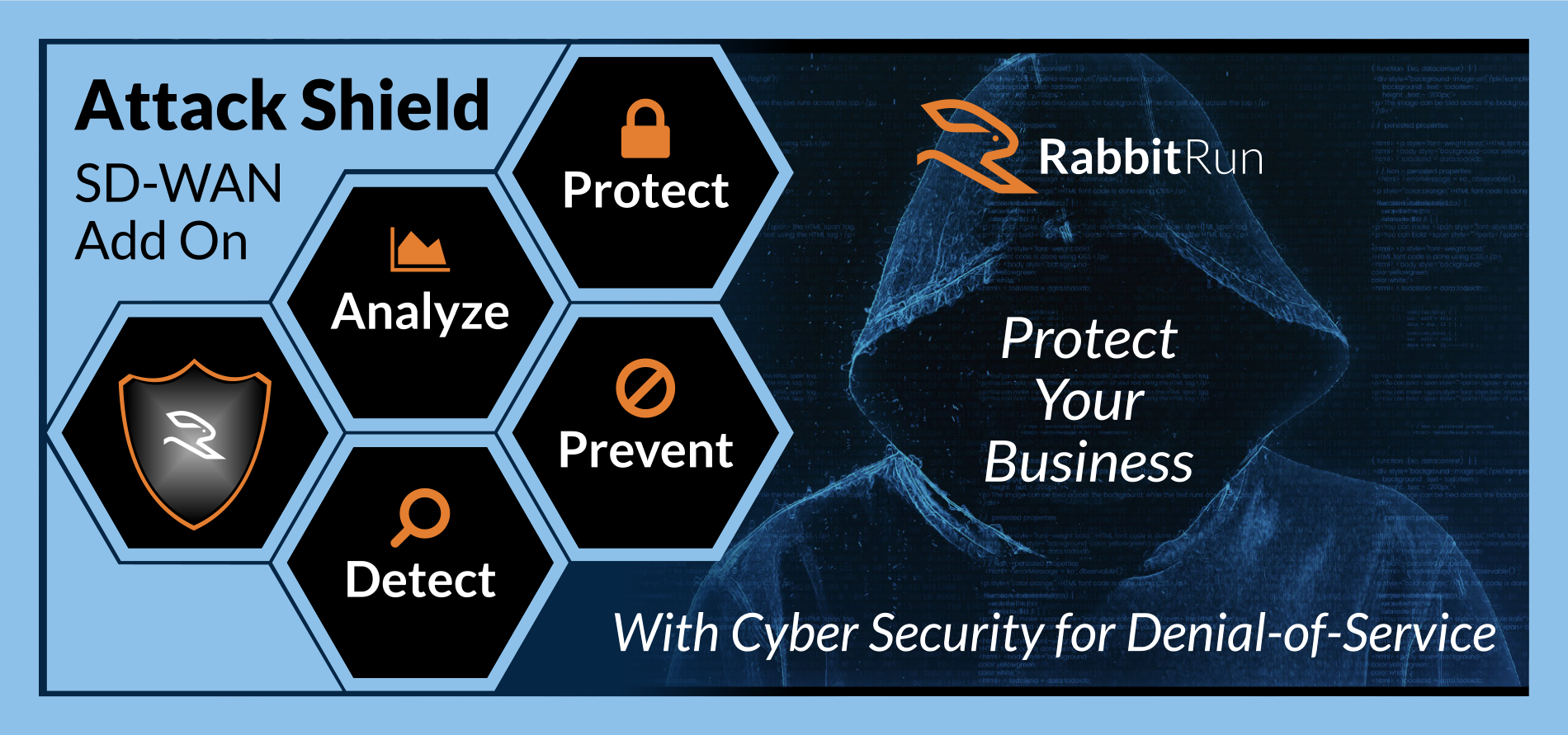
Introducing RabbitRun Attack Shield
Attack Shield is a traffic flow based analysis tool, designed for small and micro businesses facing the challenge of costly and resource intensive DDOS Cyber protection. It efficiently analyzes and manages traffic flows within the limitations of small office devices, providing a balance between effective protection and normal application operation. The solution predicts, protects, and reports on DOS/DDOS attacks.
Uses the Metadata-Traffic-Controller (MTC):
RabbitRun Technologies uses a Metadata-Traffic-Controller (MTC) to power all SD-WAN devices in a Stateful System, monitoring all traffic flows passing through the RabbitRun SD-WAN routers.
Understanding Traffic Flows:
Flows are like conversations between two points passing through or going to the device. They provide essential traffic information, including additional metadata.
System Resources:
Small office devices have limited memory, affecting the number of flows they can track. The RRT-200-LTE, in normal operation, supports a maximum of 16384 flows, more than enough for a small office SDWAN setup.
Flow Management:
Tracked flows eventually timeout, allowing new flows to form. However, relying solely on flow timeout isn’t effective against DOS attacks, and adjusting these settings can impact normal operations.
Attack Shield Features
Detect, Prevent, Protect, and Analyze Attacks
This is a new and novel approach using intelligent Traffic Flow Analysis from the SD-WAN Router’s Metadata.

Automatically Detects & Quarantines:
![]() Supports Block & Allow Lists
Supports Block & Allow Lists
![]() Handles Heavy Attack Purging
Handles Heavy Attack Purging
3 Modes of Operation & Sensitivity:
![]() Low – Catches Mostly Larger Attacks
Low – Catches Mostly Larger Attacks
![]() Mid – Catches Large to Moderate Attacks
Mid – Catches Large to Moderate Attacks
![]() Aggressive – Catches Small to Large Attacks
Aggressive – Catches Small to Large Attacks
![]() Custom – Expert Mode
Custom – Expert Mode
Inspects LAN & WAN:
The solution can also find compromised internal devices that have launched attacks to outside world targets to help protect upstream supply chain connections.
![]() Inspects World to LAN
Inspects World to LAN
![]() Inspects LAN to World
Inspects LAN to World
Cloud Portal Reports & Alerts:
Receive alerts and analyze historical state changes and attack data.
![]() Attack Alerts
Attack Alerts
![]() Attack State Change History
Attack State Change History
Find Out More & Become a Valued Reseller Partner
We offer managed network services through indirect channel partners and resellers, and our solution aligns with the challenges of smaller budgets and immediate agility requirements.