Attack Shield
SD-WAN with Cyber Security for Small Businesses
Attack Shield
SD-WAN Add On
Small businesses need affordable protection from online attacks, especially those that try to overwhelm their systems.

Traffic Flow Analysis Tool
Attack Shield is a traffic flow based analysis tool, designed for small and micro businesses facing the challenge of costly and resource intensive DDOS Cyber protection. It efficiently analyzes and manages traffic flows within the limitations of small office devices, providing a balance between effective protection and normal application operation. The solution predicts, protects, and reports on DOS/DDOS attacks.
Uses the Metadata-Traffic-Controller (MTC):
RabbitRun Technologies uses a Metadata-Traffic-Controller (MTC) to power all SD-WAN devices in a Stateful System, monitoring all traffic flows passing through the our routers.
Understanding Traffic Flows:
Flows are like conversations between two points passing through or going to the device. They provide essential traffic information, including additional metadata.
System Resources:
Small office devices have limited memory, affecting the number of flows they can track. The RRT-200-LTE, in normal operation, supports a maximum of 16384 flows, more than enough for a small office SDWAN setup.
Flow Management:
Tracked flows eventually timeout, allowing new flows to form. However, relying solely on flow timeout isn’t effective against DOS attacks, and adjusting these settings can impact normal operations.
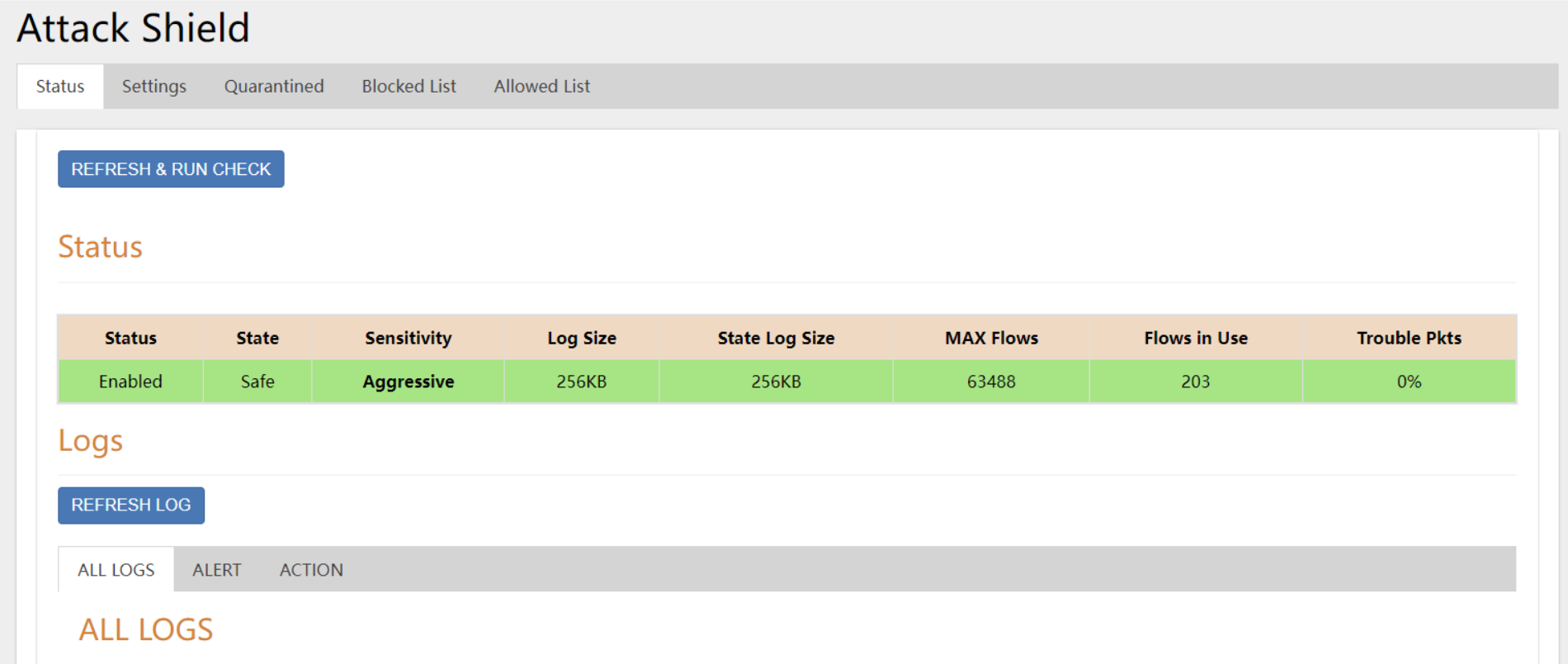
Attack Shield Features
Detect, Prevent, Protect, and Analyze Attacks
This is a new and novel approach using intelligent Traffic Flow Analysis from the SD-WAN Router’s Metadata.

Automatically Detects & Quarantines:
![]() Supports Block & Allow Lists
Supports Block & Allow Lists
![]() Handles Heavy Attack Purging
Handles Heavy Attack Purging
3 Modes of Operation & Sensitivity:
![]() Low – Catches Mostly Larger Attacks
Low – Catches Mostly Larger Attacks
![]() Mid – Catches Large to Moderate Attacks
Mid – Catches Large to Moderate Attacks
![]() Aggressive – Catches Small to Large Attacks
Aggressive – Catches Small to Large Attacks
![]() Custom – Expert Mode
Custom – Expert Mode
Inspects LAN & WAN:
The solution can also find compromised internal devices that have launched attacks to outside world targets to help protect upstream supply chain connections.
![]() Inspects World to LAN
Inspects World to LAN
![]() Inspects LAN to World
Inspects LAN to World
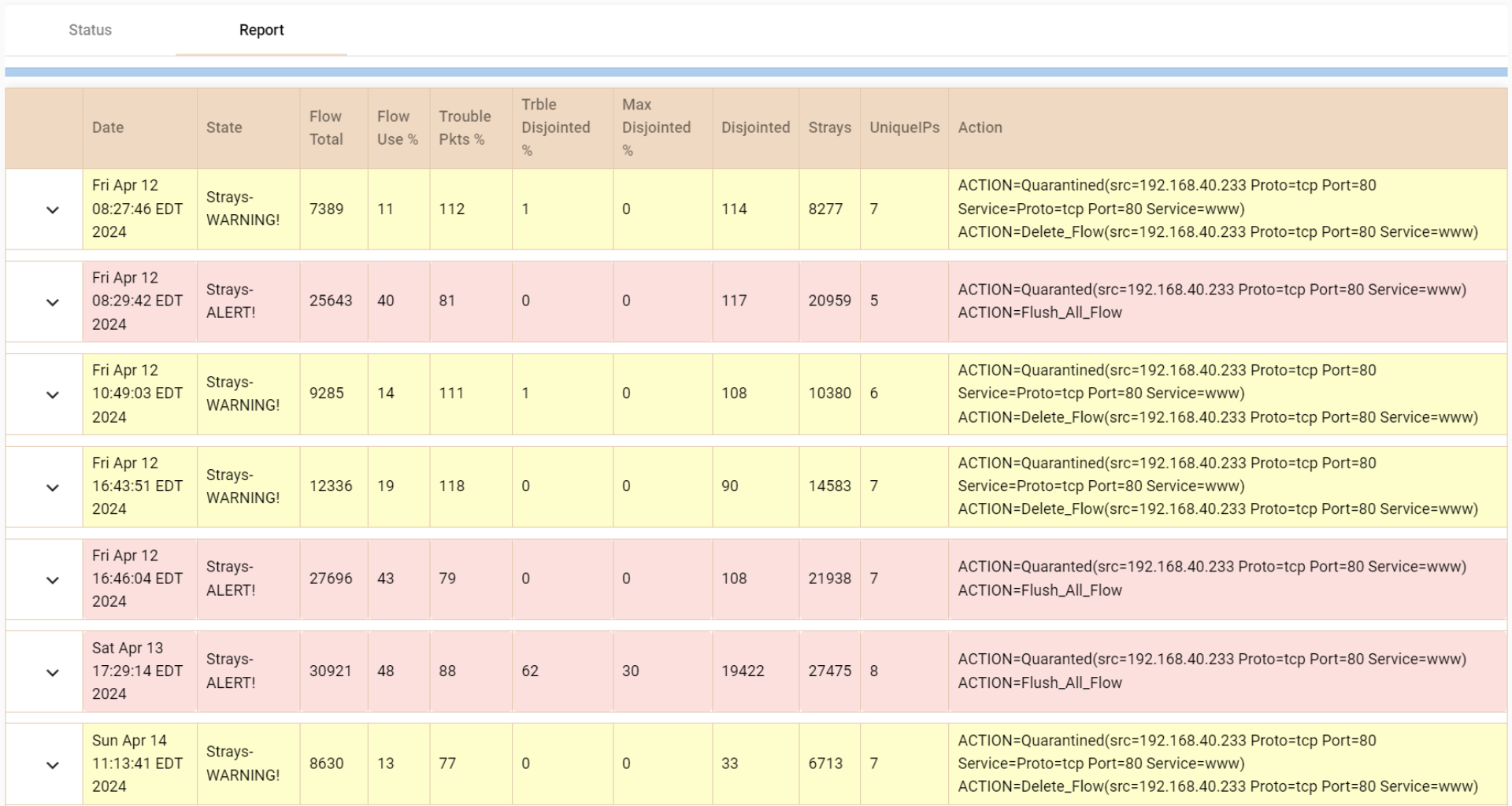
Cloud Portal Reports & Alerts:
Receive alerts and analyze historical state changes and attack data.
![]() Attack Alerts
Attack Alerts
![]() Attack State Change History
Attack State Change History
IF YOUR CUSTOMERS ARE LOOKING FOR
“ALWAYS ON VOICE & POS”, WE HAVE THE SOLUTION!